
an in-depth conversation between Global CISO and architect on today's cybersecurity challenges
Cybercrime has evolved into a trillion-dollar industry, and organizations face (or will face) unprecedented security challenges as emerging technologies such as AI and quantum computing amplify the sophistication and scale of digital threats. Our Lead Strategist, Marnix Boot, sat down with two experts:
- Cybersecurity veteran Stef Hoffman, who has a rather original background, initially worked in IT before transitioning to sales and sales management for the first half of his career. He then moved into risk management and cybersecurity, and later became Global CISO at Philips.
- Network and security architect Tim van Lanen, founder of eNTek, a valued Exellyn business partner, who also boasts an impressive resume, having served as the lead architect at Philips for a while, where he collaborated with Stef.
Together, we explored how enterprises can navigate this complex environment through strategic simplification and differentiated protection approaches. Their insight and experiences, spanning major implementations at global enterprises, offer valuable insights into transforming security from a cost center into a value-added activity, resulting in a competitive advantage.
the escalating threat landscape: beyond the headlines
Marnix: We're constantly bombarded with news about cyberattacks and data breaches. How worried should organizations really be?
Stef: "I think we must be genuinely concerned. Microsoft clients globally face attacks every second of the day - in fact, they experience 7,000 attacks per second. And that's just Microsoft clients alone."
Tim: "We need to be worried about the future, and we should already be concerned about what's happening right now."
The conversation then zooms in on the most significant threat multipliers: Artificial Intelligence (AI) and quantum computing.
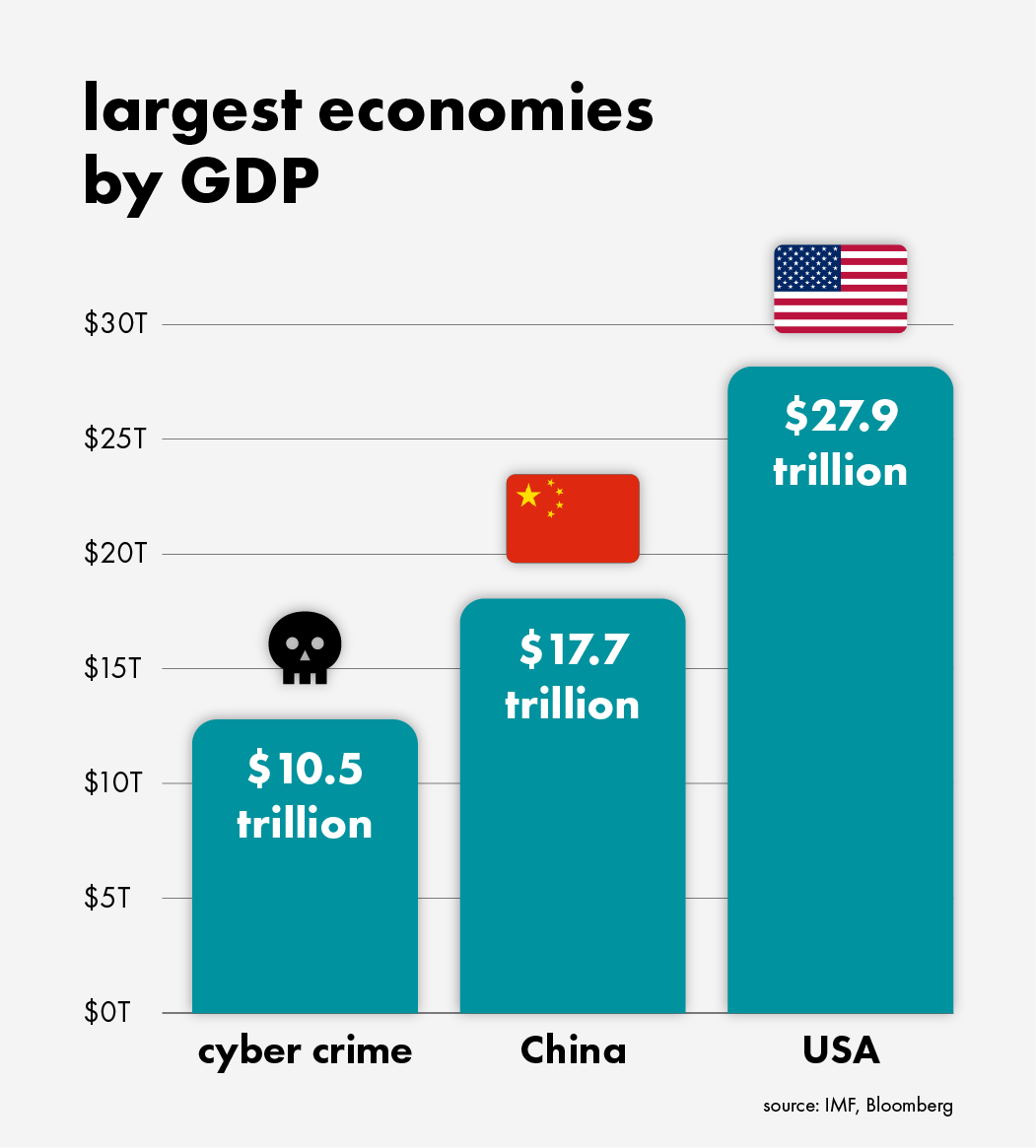
Stef: "With AI and quantum computing emerging, I believe we've only seen the first small effects in cybersecurity and cybercrime. AI and quantum (especially their combination) will transform cybercrime into an enormous business. It already rivals Google and ChatGPT in scale and impact. As a matter of fact, data shows that the cybercrime industry is already a $10.5 trillion industry. If it were measured as a country, it would simply be the world's third-largest economy, after the U.S and China.
To illustrate the quantum threat's magnitude, Stef references Google's Willow chip: "A single Google Willow chip will be 26 quadrillion times faster than the fastest GPU on Planet Earth today. Imagine building a server with thousands of those Willows - that represents more computing power than has ever existed on our planet."
Tim adds a chilling perspective: "Here's the reality: assume quantum computing and AI will be available to bad actors within six months to two years. You're already vulnerable to attacks from the future today through what we call 'store now, decrypt later' tactics."
He explains: "An attacker can intercept your encrypted communications today, store them, and wait. When quantum computing becomes available, they can decrypt data from years ago. If that information has lasting value, you're essentially compromised right now."
the criminal advantage: why attackers are winning
When asked why cybercriminals seem to have the upper hand, both experts point to a fundamental asymmetry in approach and resources.
Stef: "There's a crucial difference between legitimate organizations and cybercriminal groups. Companies and governments protect their knowledge and intellectual property because sharing it would benefit their competitors. Cybercriminals operate on ego and reputation: when they discover something new, they share it widely. They want recognition for being first to find a new exploit or malware variant."
Tim uses a powerful analogy: "Think of a large enterprise as having 10,000 doors that need protection. Attackers only need to find one unlocked door to succeed. It's less difficult for an attacker to find and exploit a single vulnerability than for an organization to secure every possible entry point."
This leads to a critical insight about AI's current impact: "We're seeing zero-day vulnerabilities weaponized within hours now, not weeks. A vulnerability was released about a year ago, and security teams detected attacks just one hour after disclosure. AI enables this speed. Previously, organizations had roughly two weeks to patch before seeing widespread attacks. With AI, that window has shrunk to minutes or hours. It is therefore imperative for organizations to design infrastructure with features such as automatic upgrades."
from cost center to value add, resulting in competitive advantage: reframing security
Rather than trying to protect everything equally, Stef advocates for a differentiated approach that transforms security from an expense to an investment — and more importantly — leads to a Return on that Investment (ROI).
Stef: "Most security teams strive to protect every one of those 10,000 doors with the strongest possible lock, even when there's nothing valuable behind many of them. My approach is to focus on maximum protection for what's truly critical for the company. For organizations like ASML, NXP, Thales, and Philips, for example, that's intellectual property."
The business case becomes clear: "If I can prevent an invention from leaking to competition for just one additional year, that translates immediately to one additional year of revenue and profit. So yes, we must protect all 10,000 doors, but the ones guarding IP should get the absolute maximum security investment."
This differentiated approach extends beyond just protecting what exists; it's also about creating a competitive advantage. When big corporations can demonstrate superior security in their products compared to competitors, it becomes a Unique Buying Reason.
the language barrier: why security fails at the C-Suite
A recurring theme emerges around communication between security teams and executive leadership.
Stef: "Security has become a C-suite responsibility (CEOs can face fines or even imprisonment for security-related incidents). However, here's the problem: most CEOs lack a comprehensive understanding of security, or they don't understand security at all. And frankly, that's often the security team's fault."
He continues: "Security professionals are technocrats using twenty abbreviations in thirty seconds, talking about components and incidents. But CEOs speak a different language entirely: they speak dollars, euros, and yuan. Security teams must express their value in financial terms, not in technical jargon about malware or attack vectors."
This communication gap has structural implications: "Most security teams still report to IT, which creates a fundamental conflict of interest: it's like having the butcher grade his own meat. Security extends far beyond IT infrastructure, encompassing behavioral aspects of every employee and vendor. Why delegate it to IT? Security should report directly to board level, whether that's the CFO, CTO, or Chief Legal Officer."
simplify to fortify: the infrastructure challenge
The discussion shifts to practical implementation, where Tim's architectural expertise becomes indispensable. He notes that modern infrastructure spans numerous specializations, making cross-domain integration increasingly complex. A best-of-breed strategy, where each solution originates from a different vendor, inevitably requires extensive integration not only to achieve but also to maintain a cohesive and reliable environment. In such cases, it becomes difficult to create additional value through integrations, as much of the effort is already consumed by simply making the various point solutions work together.
The challenge of "Best-of-Breed" versus "Best-of-Suite" approaches reveals a fundamental tension in security thinking.
Stef: An organization could choose a "Best-of-Breed" approach and invest millions in the best security components money can buy. The massive effort to integrate, implement, operate, and maintain a complex security stack will take away the focus on actual deployment. Cases show that the deployment of complicated "Best-of-Breed" could lead to a deployment of less than 10 percent. I'd rather deploy a mediocre solution everywhere than have the world's best solution protecting a minor part, and not necessarily the most important one."
This insight leads to a redefinition of security maturity: "Traditional maturity models focus on processes and functionality, essentially engineering perfection. A third component is essential: coverage. You can have the best technology on Planet Earth, yet if it's not deployed broadly, your security maturity remains low."
Tim adds practical context: "Organizations often underestimate the true cost and complexity of making disparate vendor solutions work together. There is a common assumption that products from different vendors can simply be connected and will function seamlessly. In reality, they do not. The result is that enormous resources are consumed by integration efforts rather than being directed toward delivering actual security outcomes."

the mandate imperative: organizational change management
Both experts emphasize that technical solutions alone are insufficient without organizational commitment.
Stef: "When you move to a Best-of-Suite approach, you can reallocate resources more effectively. Instead of spreading several full-time employees across relationships with numerous vendors, you can concentrate that same investment on five to ten key partnerships and help those vendors improve their products specifically for your needs."
However, this requires difficult decisions: "Standardization demands a board-level mandate. You'll have brilliant engineers in your workforce who've built unique, innovative solutions over the years. The painful reality is that you must set those aside to adopt enterprise standards, regardless of how well they worked in the past."
Stef acknowledges the challenge: "Abandoning your own innovations is emotionally difficult. Sometimes you need a crisis —a major security incident or extreme cost pressures— to create the platform for necessary change."
the digital convergence: IT and OT integration
As physical systems become digital, new security challenges emerge, particularly in operational technology (OT) environments.
Tim: "Think about traditional manufacturing: a diesel motor running supply chains, people working manually to build products. You couldn't hack that system because it wasn't digitized. But we're now entering the era of smart manufacturing, where organizations want end-to-end supply chain visibility and the ability to optimize factory performance in real-time."
The security implications are significant: "The evolution typically happens in two phases: first, monitoring factory systems for optimization data, then remotely controlling individual components. Each phase introduces new vulnerabilities that didn't exist in purely physical systems."
Stef provides strategic guidance: "You need a clear demarcation between IT and OT environments, defining exactly where each domain starts and ends. At the intersection point, implement the most stringent security measures possible to prevent violations from crossing between domains."
Tim offers a practical solution: "We implement what we call OT gateways or manufacturing gateways. These gateways control exactly what information flows in and out at the granular level. When something goes wrong, you can completely cut the gateway connection. This approach avoids having hundreds of different connection points scattered throughout the facility."
the path forward: preparing for an uncertain future
As the conversation concludes, both experts return to the urgency of preparation.
Stef: "Everything physical is becoming digital (work, crime, warfare, even social interaction). Physical crime has moved online because why steal a bicycle in the rain when you can hack from home with snacks and a comfortable chair? This digitization dramatically expands the target landscape for cybercriminals every single day. Cybercrime has become a full-blown business."
The call to action is clear: "Cybersecurity represents what I call a 'grey swan' event, something we can imagine but don't believe will actually happen. Organizations still have time to prepare for AI and quantum threats, but we must start now. Today is the moment to begin."
Tim adds practical urgency: "Organizations can't wait until these technologies are available to bad actors before beginning preparations. Transforming infrastructure for a global enterprise, strengthening encryption protocols, and updating embedded systems takes years of planning and implementation."
key takeaways
- complexity is the enemy of security: Overly complex, non-standardized, and fragmented systems are impossible to protect from a security perspective.
- differentiated protection: Maximum security for existential (information) assets, appropriate security for everything else.
- coverage over perfection: Better to have adequate protection everywhere than perfect protection "nowhere".
- executive communication: Security teams must articulate value in business terms, not technical jargon.
- standardization imperative: True security requires an organizational mandate to eliminate deviations and complexity.
- partnership over procurement: Deep relationships with fewer vendors deliver better outcomes than scattered point solutions.
Enjoying this article?
Follow expert insights,
industry trends, and more
in our quarterly newsletter!
share with your network
click here to download







